Singapore: New advisory guidelines to strengthen resilience of cloud services and data centres
-
Bulletin 11 mars 2025 11 mars 2025
-
Asie-Pacifique
-
Technologie et évolution de l’IA
-
Cyberrisques
Singapore: New advisory guidelines to strengthen resilience of cloud services and data centres
The Singapore Infocomm Media Development Authority (“IMDA”), have, in two advisory guidelines dated 25 February 2025, issued best practices on the resilience and security of Singapore’s compute infrastructure, namely Cloud and Data Centres.
The advisory guidelines are:
- The Advisory Guidelines for Resilience and Security of Cloud Services (“AG for CS”); and
- The Advisory Guidelines for Resilience and Security of Data Centres (“AG for DC”).
For Cloud Services, the AG for CS covers 7 categories of measures to uplift the security and resilience of Cloud Services. Measures that CSPs are encouraged to implement relate to areas such as security testing, user access controls, proper data governance, and planning for disaster recovery.
For Data Centres (“DC”), the AG for DC provides a framework for operators to put in place a robust business continuity management system to minimise service disruptions and ensure high availability for their customers. This includes guidance on implementing business continuity policies, controls and processes, and continuously reviewing and improving them. The AG also sets out measures to address cybersecurity risks in DCs.
Cloud service providers (“CSPs”) and data centres operators (“DCOs”) are encouraged to designate an officer (such as a senior representative) to take charge of implementing the measures.
In this client update, we summarise the key aspects of the two advisory guidelines.
AG for CS
The measures are organised into 7 categories, and are in line with existing international standards (such as MTCS, ISO 27001 and CCM), with some additional measures to better address risks.
| Category | What does it generally cover? |
| 1. Cloud Governance |
|
| 2. Cloud Infrastructure Security |
|
| 3. Cloud Operations Management |
|
| 4. Cloud Services Administration | CSPs should implement cloud services administration controls to ensure the enforcement of policies, standards and procedures relating to the creation, maintenance and removal of privileged accounts used for managing cloud services and supporting networks. |
| 5. Cloud Service Customer Access | CSPs should implement cloud user access controls to ensure that policies, standards and procedures are established and implemented to govern the creation, maintenance and removal of user accounts to restrict access and safeguard user credentials to prevent unauthorised access to information and information systems. |
| 6. Tenancy and Customer Isolation | CSPs should implement tenancy and customer isolation controls to restrict user access within the same physical resource and segregate network and system environments such that the customers do not pose a risk to one another in terms of data loss, misuse and privacy violation. |
| 7. Cloud Resilience |
|
AG for DC
There are 3 main key risks – (1) DC infrastructure; (2) Governance; and (3) Cyber.
| Risks | What does it generally cover? |
| 1. Infrastructure Risk |
These are risks stemming from insufficient consideration of risk in the design of DCs. The key risk areas are:
|
| 2. Governance Risk |
These are risks stemming from insufficient risk oversight of DC operations. The key risk areas are:
|
| 3. Cyber Risk |
These are risks of cyberattacks on DC operating systems and controls E.g., risks of data centre infrastructure management systems being compromised which may result in unauthorised temperature changes due to inadequate cybersecurity control measures. |
To manage the above risks, DCOs should adopt the following process:
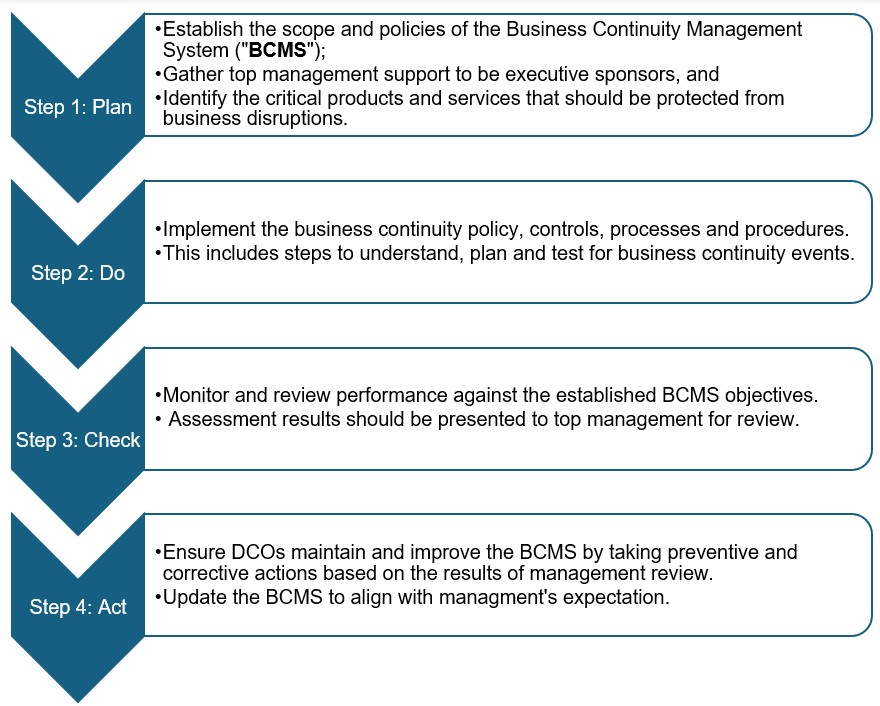
Concluding remarks
The advisory guidelines are an additional step to boost the resilience and security of Cloud Services and DCs, following the amendments to the Singapore Cybersecurity Act last year to address the cybersecurity risks of such digital infrastructure.
Additionally, the advisory guidelines complement the upcoming introduction of a new Singapore Digital Infrastructure Act (“DIA”), which will regulate systemically important digital infrastructure such as major CSPs and DC operators.
The advisory guidelines, along with the upcoming DIA, will bolster infrastructure resilience for cloud services and data centres, and create a more secure and reliable digital environment for businesses and consumers.
How we can help
As a dynamic, global law firm, Clyde & Co provides expert advice to our clients on digital laws and regulations, complex IT outsourcing and procurement agreements, and data protection compliance issues that arise out of their projects. Our team of seasoned specialists also provides expert advice on how to address compliance risks, navigate crisis response, and respond to data protection and privacy issues across the full cyber lifecycle.
To discuss how this latest regulatory development may mean to you, please feel free to reach out to the author below.
Fin