A Round Up of Data Breaches 2024 – A Summary of PCPD Reports and What Organisations Can Do to Protect Themselves
-
Insight Article 08 January 2025 08 January 2025
-
Asia Pacific
-
Tech & AI evolution
-
Cyber Risk
The Privacy Commissioner’s Office published six investigation reports in 2024, revealing common problems among Hong Kong organisations’ IT systems and data protection measures.
THE LANDSCAPE
Starting from the year 2022, we have seen increasing occurrences and severity of data breaches in Hong Kong. While we await the release of the latest statistics on data breach notifications, according to the Privacy Commissioner’s Office (the “PCPD”), since September 2024, there has already been a total of 155 data breach notifications. It will certainly not be surprising if the number of data breach notifications received in 2024 surpass those of 2023.
There is likely a significant number of non-public data breach incidents known to the PCPD given the current voluntary notification regime in Hong Kong. Although the PCPD has been proposing reform of the notification regime for years, establishing a mandatory data breach notification mechanism remains one proposed amendment to the Personal Data (Privacy) Ordinance (the “PDPO”) in the Reports on the Work of the Office of the Privacy Commissioner for Personal Data 2022[1] and 2023[2]. While the PCPD is still formulating proposals for the amendments, the regulator is adopting a stricter approach and is becoming more active in enforcing the PDPO.
The PCPD’s enforcement focus is reflected in its published investigation reports. In 2024, the PCPD issued a total of six investigation reports, reflecting a sharp increase when compared with only one report issued in 2023.
DATA BREACH INCIDENTS SUMMARY
The six investigation reports cover data breach incidents suffered by (i) Hong Kong Cyberport, (ii) the Consumer Council, (iii) Hong Kong Ballet Limited, (iv) the Council of Hong Kong Laureate Forum Limited, (v) South China Athletic Association and (vi) the Electrical and Mechanical Services Department. Apart from the Electrical and Mechanical Services Department data breach incidents, all of the remaining data breach events were a result of ransomware attacks.
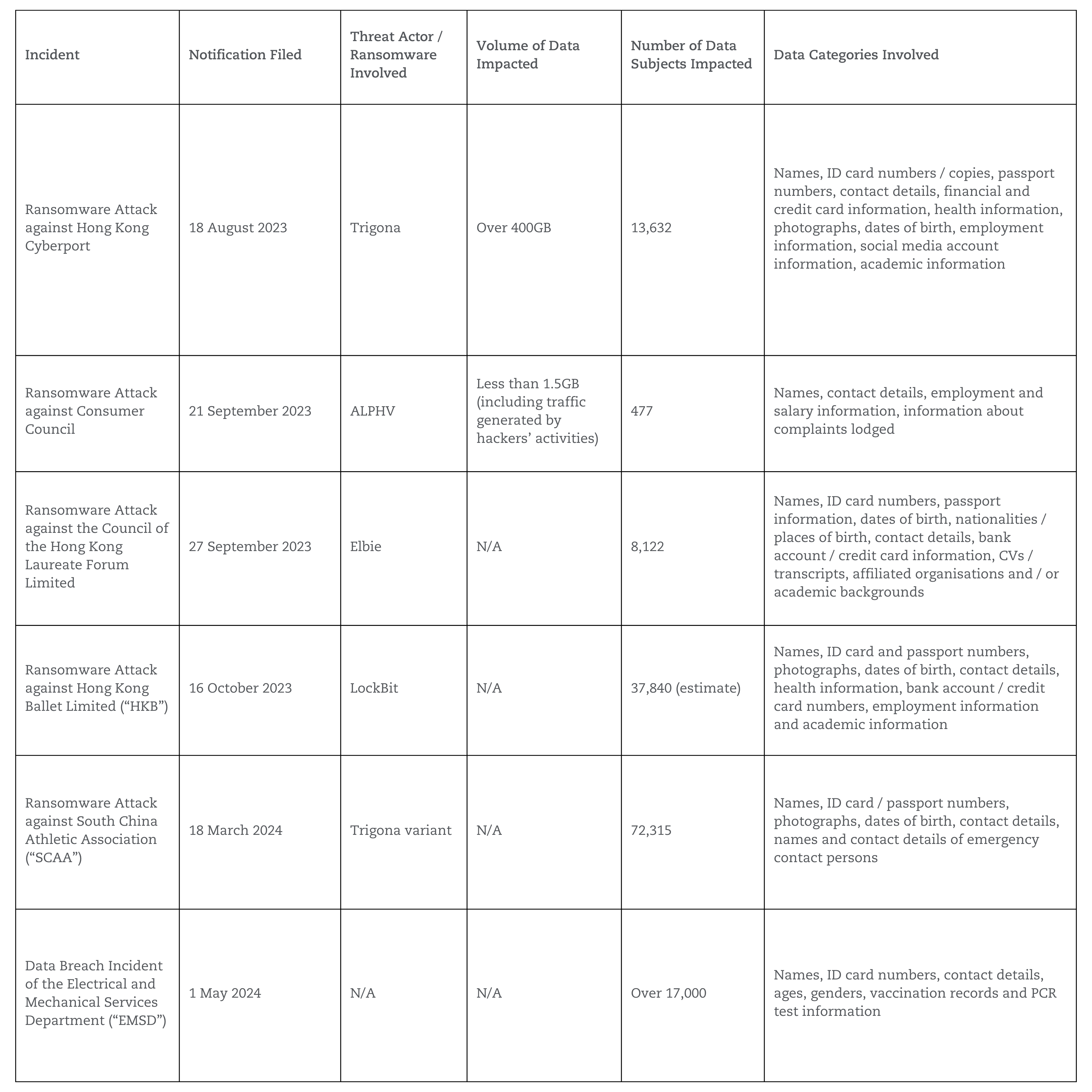
SUMMARY & COMPARISON OF FINDINGS
Incidents investigated by the PCPD in 2024 arose from both internal and external cybersecurity failures of the organisations themselves and third-party service providers they engaged. Based on the six investigation reports, there are some important lessons for organisations to protect themselves from cyberattacks and data breaches.
One common cause among the six incidents is the lack of a comprehensive IT policy. For example, the PCPD criticised Hong Kong Cyberport for not having specific requirements regarding virus protection controls in its 41-page “Cyberport Information Security Policy”. More traditional organisations such as the SCAA had not formulated a written password policy setting out password complexity requirements. The absence of policies and guidelines detailing responsibilities of different personnel, work procedures and IT security requirements meant that staff members and contractors had nothing to refer to nor to comply with. This leaves the IT systems open to compromise, which allow hackers to take full advantage. Worse still, not having a detailed IT policy also means organisations are not prepared for any cyberattacks, increasing not just the risk of cyberattacks but also the materiality of losses caused by these cyberattacks.
One very direct cause of systems vulnerability is the failure to enable Multi-Factor Authentication (“MFA”). Hong Kong Cyberport, Consumer Council and the SCAA failed to enable MFA for administrative accounts, which gave hackers easy access to the system without any additional identity verification steps. Without implementing MFA, organisations’ IT systems become open doors, which allow hackers to navigate the systems environment, instal malware and launch attacks.
The PCPD also criticised a number of organisations for insufficient or irregular security audits of their IT systems. Too often, organisations ignore the importance of auditing their IT system security, and hence fail to detect IT security vulnerabilities. Take the Council of Hong Kong Laureate Forum Limited incident as an example, the failure to conduct security audits led to its subsequent failure to apply updates to patch multiple system vulnerabilities, conferring ample opportunities to threat actors to exploit these system deficiencies.
Meanwhile, the HKB and EMSD incidents show that loose supervision of compliance with data protection obligations by third-party service providers can lead to material privacy breaches. Managing third-party vendors is a universal obligation, but it is too often assumed that the burden of data protection obligations has also been shifted to the third-party IT specialists. For instance, the HKB failed to ensure its vendor updated software and installed patches on a timely basis - whereas the EMSD failed to follow up with the contractor on deletion of data.
One crucial aspect highlighted by the Cyberport incident is that failure to have appropriate data retention policy in place greatly increases the risk of data breach and intensifies the materiality of infiltration. While most organisations would, naturally, focus on collection and actual processing when dealing with personal data, we should never forget that retention of data is also part of the data processing cycle. Cyberport held personal data of more than 5,000 individuals beyond the corresponding retention periods, and therefore accentuated the high number of individuals impacted by the incident. The same logic applies to the EMSD incident, although it is a third-party contractor scenario – had the EMSD taken the initiative to ensure its contractor was deleting personal data on a progressive and timely basis, the number of individuals affected would have been greatly reduced.
Ultimately, all of these causes can potentially be attributed to the overarching issue of lack of awareness among organisations and their people. According to the Hong Kong Enterprise Cyber Security Readiness Index and AI Security Survey[3] conducted by the Hong Kong Productivity Council and the PCPD in 2024, the Hong Kong Enterprise Cyber Security Readiness Index remains at the “basic” level, as it scores 52.8 out of 100 points. This bare passing score means organisations in Hong Kong are not well-equipped with the necessary cybersecurity capability and are not sufficiently well-prepared for attacks. This survey found that Hong Kong enterprises are particularly weak at “human awareness building”, such that organisations should spend more time and effort in conducting security awareness education, cybersecurity drills and promoting risk culture within the organisations.
WHAT ORGANISATIONS SHOULD DO IN 2025
The key to prevention of cyberattacks and data breaches is to keep and maintain resilience of the organisations’ IT systems.
Organisations should:
- Maintain detailed IT security policies, covering at least the basic aspects such as IT security structure, password policies, access control policies, incident management plan, IT services outsourcing policies as well as data backup policies;
- Ensure that all staff in the organisation read and understand the policies, and that these policies are readily accessible to staff members at any time. More importantly, these policies should not only exist on paper, but they have to be implemented.
To get prepared for cyberattacks, the first step is to understand the organisations’ risk profile and formulate response strategies accordingly. Organisations should ask themselves:
- What and whose personal data do they collect?
- What is the purpose of collecting these personal data?
- For how long should these personal data be kept? Detailed analysis on the extent of business interruption caused by cyber incidents of different degrees of intensity allows organisations to respond promptly and appropriately to various scenarios and seek to minimise loss and damage.
Organisations should also bear in mind the importance of having a set of clear, consistent and transparent communication strategies so as to manage stakeholders’ expectation in case there is a data breach incident.
Besides all the internal measures, organisations should also be aware of third-party service providers’ data protection obligations. Make sure there are provisions in service contracts obliging the service providers to comply with relevant legislation, imposing additional data protection obligations on the contractors when necessary. Ideally, conduct an audit on the capacity of the contractor in complying with these statutory and contractual data protection duties. Under the current PDPO regime, organisations being the data users bear the ultimate responsibility to ensure data security at all levels.
Both the statistics and the investigation reports released by the PCPD point to the same conclusion – cyberattacks and data breaches are becoming increasingly prominent risks, threatening business operations in Hong Kong. Organisations should also consider having a cyber insurance policy in place which shields them from losses and damages caused by cyberattacks, especially when most insurers provide a one-stop cyber service. If organisations have already taken out cyber insurance, revisit the policy and make sure the cyber insurance package covers what the organisations need.
Lastly and also the most fundamental measure is making sure everyone in the organisations is equipped with the most up-to-date knowledge of legal, regulatory and technological developments. This is especially important when the Hong Kong Cybersecurity Law introduced, requiring additional data breach response obligations from designated organisations. To cultivate a cybersecurity-aware environment, organisations need to provide training and education sessions regularly to their staff members.
With the backdrop of the impending introduction of the mandatory data breach notification regime and the endless array of more complicated cyberattack techniques, underprepared organisations are putting their business operation, reputation or even continuity in jeopardy.
For more information regarding cybersecurity and data privacy law, you may get in touch with Simon McConnell and his team's specialists - Michelle Ho and Fiona Cheng.
End